Q&A: How To Prepare For the Cyberattack That’s Coming – Or May Have Already Been Launched
Cleveland-based Fortress Security Risk Management is on the front lines of the cybersecurity wars with the goal, as Fortress puts it, of “protecting companies from the financial, operational, and emotional ravages of cybercrime.”
As Forbes reported earlier this year, businesses suffered 50% more cyberattack attempts per week in 2021 and they are accelerating in 2022. And not surprisingly, cyber incidents now are the No. 1 concern for companies globally, according to the Allianz Risk Barometer.
We asked Chuck Mackey, Director, Cybersecurity Consulting at Fortress, to talk about some of the trends and to help get our heads around some of the frightening numbers.
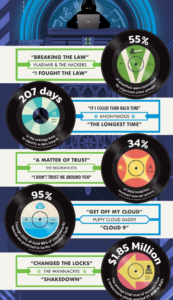
So, we thought your “Hacker’s Jukebox” graphic was a creative way to deliver some eye-opening news about cyberattacks. The number that most jumped out at us was that, on average, it takes 207 days for an organization to even identify it’s had a data breach. How can that be?
Most companies either don’t believe they are a target or don’t invest in some relatively affordable tools and services to attain a high level of protection.
The FBI cyber team tells us there are only two types of companies: those that have been breached and those that have been but don’t know it. The bad actors, primarily well-funded criminal gangs, are using exceptionally clever technical tools and behavioral tricks to get into an organization’s network. Once in, they lay in wait learning about who’s who, what valuable information can be pinched and sold on the dark web like intellectual property, employee Social Security numbers, addresses, birthdates, health info, what the company’s financials are, do they have cyber insurance, etc.
Often, if there is a sizeable transaction occurring, they will spoof the CFO’s email and have the controller or accounts payable person change the routing number and send that payment to the bad actor’s bank. This is called Business Email Compromise. Or they may launch a ransomware attack and encrypt the company’s network essentially stopping all activity.
OK, so we’ve hit Day 207 and we realize we’ve been breached. What do best practices say is the first, most important step to take?
If it’s a ransomware attack, there are several people to call. First, your attorney or outside counsel who has cyber experience. You need an attorney to be the “breach coach” to run the response and have your legal back. Second, a security company like Fortress that works with the attorney and under attorney-client privilege to advise on the technical steps to take to minimize the damage and contain the malware. Third, if the company has cyber insurance, the insurance broker. And don’t overlook the fact that your employees, customers and other key stakeholders will hear about this and will want to know what is going on – fast. Look for help from communication professionals, like all of us at Hennes Communications, who have experience anticipating the questions that come after a cyber attack and how to answer effectively.
It’s always a good idea to have established relationships with these folks as well as the local FBI office well before an attack occurs. If you have to start figuring out who to call and what to do during an incident it will be incredibly more painful.
Has the massive shift of people working from home during the COVID-19 pandemic affected cybersecurity? Made it better or worse? Because we’re betting on worse.
Certainly the mass shift to remote has exacerbated security concerns and has increased vulnerability across the board. Inside the corporate office, for the most part, people and their data are better protected than at home. At home, many people do not have a VPN (virtual private network) that encrypts their data. Family members may be using the work computer. The work computer may be used for non-work activities. People may be more relaxed and more “security complacent” at home or on the go. Also, being mobile means tapping into Wi-Fi at various public places. All more dangerous. But one of the simplest solutions is mandating and implementing organization wide multi-factor authentication and solid passwords of 10 or more letters, numbers, and symbols.
Here’s another number from your Hacker’s Jukebox: $1.85 million. That, Fortress notes, is the average total cost of recovery from a ransomware attack in 2021. What are some of the costs that go into that number that people might not immediately think about?
Sadly, the average cost has gone up in 2022. We are looking at ransom demands in the $300,000 area and the ransom payment accounts for only about 15% of the total cost of a ransomware attack.
Some of the other cost centers are: business interruption and lost productivity (average downtime from a ransomware attack is 21 days); lost current business and long-term contracts; legal and litigation costs, which can be intense, depending on the business and state regulatory fees, notifications, and credit monitoring if personally identifiable information is stolen; the incident response, disaster recovery and remediation and the cost of additional security services to ensure it doesn’t happen again.
And those are the “hard” costs. Then there are the costs that are more difficult to compute but that we know come with a cyberattack. There’s reputational and brand damage – 59% of consumers said they would avoid doing business with a company that had a cyberattack in the last year, according to one survey. Damage can be done to vendor and partner relationships – 63% of companies have no 3rd party vendor safeguards. And finally, there’s the hit to employee morale and recruitment.
If a company has insurance, a business interruption policy may cover some of this. But it’s critical before the attack to really examine your policy and know what it covers. Cyber insurance is the last resort and it’s important to have but given the eye-popping rate increases we’re seeing along with lower coverage and more stringent requirements from the carriers, you really need to understand the coverage.
We saw that CBS News, citing Boston-based Cybereason, reported 80% of organizations that previously paid ransom demands said they were exposed to a repeat attack. Frankly, that makes it sound hopeless. What do you tell organizations that have suffered a ransomware attack to do to avoid another attack?
It’s not hopeless at all. The key is improving your cyber maturity and resiliency.
The bad guys always leave virus payloads behind to hibernate and launch at a future date – thus another attack. Many victims don’t take the important step to clean those out fully after the first attack. Your security company, through digital forensics, can clean them out.
Here is where the FBI can be helpful as they have a huge database on the TTPs (tools, tactics, procedures) of numerous criminal gangs and might be able to alert you to where the perpetrators have left their latent viruses.
After a hit, the victim should take a holistic view of their security maturity, improve it, and if attacked again will be able to either repel the attack completely, contain it to a few machines, or have a level of resiliency that means it will hurt a lot less than the first time.
About Fortress:
Fortress Security Risk Management protects companies from the financial, operational, and emotional ravages of cybercrime by enhancing the performance of their people, processes, and technology. Offering a robust co-managed solution to enhance an internal IT team’s capability and capacity, Fortress features a full suite of managed security services (SOC, patching, EDR, backups) plus specialized services like Cybersecurity-as-a-Service, Incident Response including disaster recovery & remediation, M&A cyber due diligence, identity & access management, threat management, vulnerability assessments, and technical testing. With headquarters in Cleveland, Fortress supports companies with both domestic and international operations.
In Case of Emergency:
Cyber Attack Hotline: 888-207-0123 | Report an Attack: IR911.com
For Preventative and Emergency Resources, please visit:
RansomwareClock.org
To reach Fortress Security Risk Management https://fortresssrm.com call or email Peter Cavrell, 440-268-3141 or pcavrell@FortressSRM.com
And if you’re looking for help with crisis communications around a cybersecurity attack – or any crisis – contact Thom Fladung, managing partner of Hennes Communications, at fladung@crisiscommunications.com or 216-213-5196.